Secure cloud services for document imaging automation with patent-pending identity management and encryption technologies.
The trends for TWAIN Direct document scanning
As anticipation continues to grow for the public release of the TWAIN Direct specification, the marketing team of the TWAIN Working Group are busy working on some compelling awareness and technical campaigns. Therefore, since the forthcoming specification will reveal many more details, for the purpose of this article we would like to focus on business justification for ‘The trends for TWAIN Direct document scanning’.
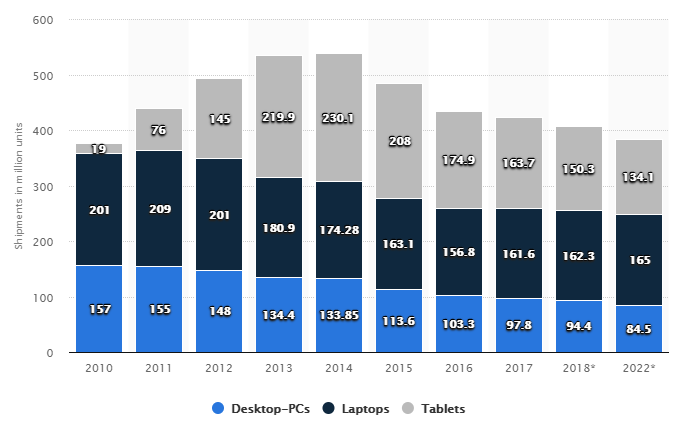
Shipment forecast of tablets, laptops and desktop PCs worldwide from 2010 to 2022 (in million units)1
The first rather obvious trend is the decline in usage of laptop and desktop PCs. With more communication and productivity options such as smartphones, tablets, voice assistants as well as other electronic appliances, the need for PCs is decreasing. In fact, this trend of communication ‘directly’ from a software application to a device, such as a document scanner without the need for a PC, is one of the main reasons that the TWAIN Working Group has been working so hard on developing the modern specification of TWAIN drivers with TWAIN Direct.
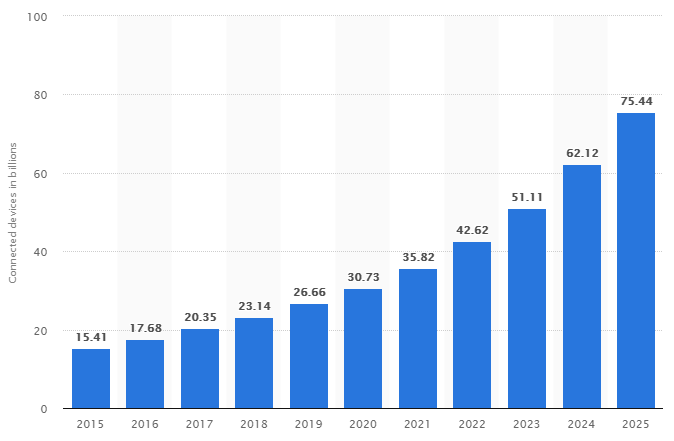
Internet of Things (IoT) connected devices installed base worldwide from 2015 to 2025 (in billions)2
Although laptop and desktop PC usage is in decline the need for hardware devices still exists, and more than ever in fact. These PC devices are being replaced by Internet of Things (IoT) devices such as document scanners that have ‘direct’ network-attach capability, e.g., WiFi and/or Ethernet connections. It is forecasted that in 2025 there will be over 75 billion IoT devices worldwide, up from just over 23 billion in 2018, a CAGR of 18.4% annually.
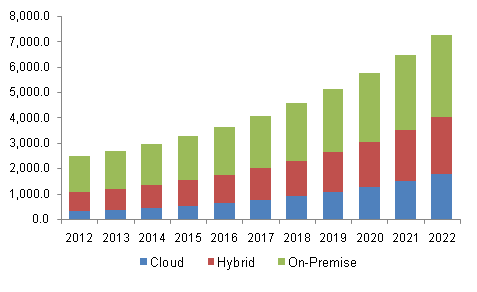
U.S. identity and access management market share by deployment, 2012 – 2022 (USD Million)3
The driving force for these two trends (decline in PC usage and increase in IoT devices) is all the benefits of cloud computing services. The business value that can be derived from a document scanning application that connects to a variety of cloud services to fit a specific organization’s needs is of great benefit to because no one size fits all. However, these new types of cloud and hybrid document scanning software applications present certain software design considerations that must be addressed.
One design consideration that we haven’t had to traditionally focus on previously is user authentication (or, ‘identity and access management (IAM)’). For example, in order for a cloud service to know who you are it needs to know your ‘identity’ in order and store your scanned images in the folder you specify. Therefore, as simple as it sounds, you must now log into your application and this is the identity part of IAM which is not necessarily anything specific to anything security-related and just makes using cloud applications logical and simple to use.
The trend towards IAM, driven by IoT and cloud, is explosive as we’ve shown however in reality, and especially with document scanners, environments are always going to be some mixture of hybrid computing and not 100% cloud. This is obvious because a physical network-attached scanner is an IoT device, typically on a corporate network connecting to a cloud service on another network. This is the very definition of hybrid computing.
While the trends clearly show high growth for cloud services, it’s interesting to note that organizations still choose to control their own identities with on-premise or hybrid identity and access management services. In these cases, one example of a popular configuration is the use of Single-Sign On (SSO) where organizations use their existing on-premise username/password authentication system, controlled by the businesses themselves. Yet at the same time utilize commodity cloud services for compute resource, networking and storage. With this SSO approach organizations can benefit from the cloud, yet still maintain control over their users’ credentials without giving complete access to cloud providers. This is the concept of Bring Your Own Identity (BYOI) to cloud services.
The business value of TWAIN Direct by being ahead of technology trends
In summary, let’s dissect each one of these technology mega trends and provide a tangible business justification.
First of all, with TWAIN Direct the driver is embedded on the scanner itself drastically reduces costs and complexity. There is obviously no need to purchase a PC and all the associated software with that PC. Also, those dreaded USB connection errors and conflicts are all eliminated which greatly reduces technical burden and provides much better user experiences.
Secondly, by being able to use whatever IoT device you wish such as a native smartphone application, web-browser client or even voice assistant instead of a thick-client USB-connected scanning application, this provides a much higher level of user productivity because they can scan documents at any time, anywhere and from whatever device they wish.
Finally, using modern identity and access management technologies, especially IAM with Single-Sign On (SSO) capability, makes document scanning applications more secure as well as provides greater compatibility with many different applications for improved business productivity.
Given this technology convergence of these three technology mega trends, forward-thinking organizations and software developers have a wonderful opportunity to design innovative document scanning applications. Using TWAIN Direct, organizations can reduce operational costs by eliminating PCs, provide better user experiences with IoT and improve overall security with IAM/Single-Sign On (SSO).
Sources:
1. Forecast: global shipment of tablets, laptops and desktop PCs 2010-2022, https://www.statista.com/statistics/272595/global-shipments-forecast-for-tablets-laptops-and-desktop-pcs/
2. Internet of Things - number of connected devices worldwide 2015-2025, https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/
3. Identity And Access Management (IAM) Market - Growth, Analysis and Forecasts To 2022, https://grandviewresearchinc.blogspot.com/2015/11/identity-and-access-management-iam.html